OSCP Review
July 23, 2018

Dedication: To my incredible girlfriend who put up with the craziness of these past few months and made sure I stayed fed and hydrated on exam day. I couldn't have done it without her.
If you’ve been in the offensive security community for any length of time then you’ve definitely heard about the OSCP (Offensive Security Certified Professional) certification. Depending on who you ask it can be considered one of the most challenging certifications in the Information Security industry (But we can talk about that later).
I recently took home the prize and completed the OSCP certification for myself. Overall it was a great experience and I consider getting root on every exam machine a personal achievement. I wanted to take a moment and share my thoughts on the experience and perhaps help an aspiring OSCP.
Outline of the OSCP
The OSCP is a 3 part journey. There is the course, the labs, and the actual exam.
The course, known as the “Penetration Testing with Kali Linux” course or PWK is a series of videos and a written manual that cover the very basics of penetration testing.
Next are the labs, and this is the heart of the entire OSCP experience. There are many systems across a variety of subnets for the student to explore. When you first start the lab time, you will be given access to the public network. From there you need to make your way into the IT, Dev, and Admin networks. The Admin network is your “end goal”.
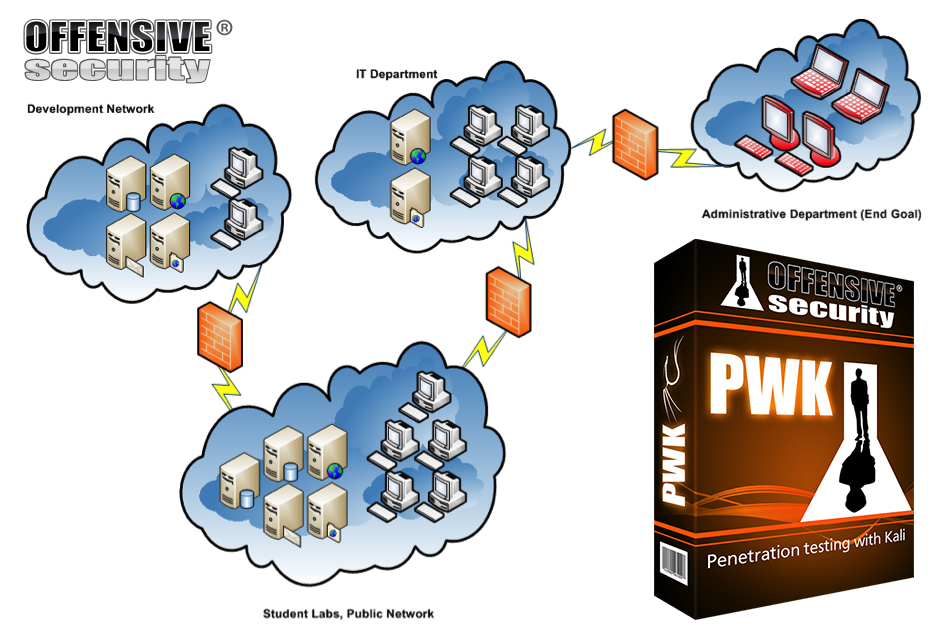
These systems offer a variety of challenges which can take the average student anywhere from a few minutes to several days to complete.
The final part of the OSCP is the actual exam, which is a 24 hour marathon to hack as many machines in the exam network as possible and submit a report based on your findings.
Who Should Pursue the OSCP?
Due to its reputation as being the “go-to” penetration testing certification, it’s a no brainer that aspiring penetration testers should go after it. Beyond that, I think it would be genuinely beneficial for defensive security types to also pursue it. The course/cert are very helpful in teaching the student “how” to attack a network. While the technology may be different, the concepts of enumeration and exploitation remain the same.
If you are in a technical defensive security role and want to go the extra mile to understand how your adversaries operate, I would recommend you pursue this certification.
What Will I Learn?
The student will learn the very basics of what it takes to perform a penetration test. This will cover reconnaissance, enumeration, exploitation, and post-exploitation. The labs are very straight forward and for the most part the student does not need to be concerned with AV, IDS, IPS, or other defensive technologies.
For more information please see the course syllabus.
What Should I know Going In?
This is something I’ve seen a lot of people talk about online. In all honesty you can prepare for the OSCP simply by practicing with VulnHub or Hack the Box. The OSCP is an introductory certification and free resources like those mentioned would be excellent. You may even notice that some of those systems are similar to boxes you will find in the OSCP labs. This is an excellent list of systems that are similar in difficulty to many OSCP machines.
In terms of networking experience you should understand what an IP address is, what a port is, and some basics regarding firewalls.
Do I Need to Know How to Code?
This is kind of a tricky question. If you have basic scripting skills then you should be fine. The only times I needed to use development skills were when I was creating basic scripts to accomplish tasks. I will say however, when you are modifying a public exploit (like ones from the Exploit Database) you may need to modify the logic of the exploit so that it will run. In one particular case, had I not read through it all the way it would have broken my shellcode and I wouldn’t know why it wasn’t working.
I’m sure every student will have their own experiences however I would advise you to at least know a little Python before you go in.
How Are the Labs Different Than VulnHub or Hack The Box?
This was something I questioned before going in and the response is simply, “they are similar”. You will find that a lot of VulnHub/HTB systems are designed to be CTF’s. As a result, those are more focused on being a fun challenge. The inverse is true with the OSCP labs, those systems are trying to be a real word (or close to it) scenario. That realism is actually beneficial because it gives the student an opportunity to see realistic environments.
For the non-CTF VulnHub and Hack the Box VM’s there is almost no difference between that and the labs.
GPEN vs OSCP
This is something I’ve been asked several times so I figured I should document it here. “Which is better, the GPEN or OSCP”. Now that I have both certifications I would strongly say that the OSCP is hands down the better certification.
To be fair, the OSCP had the advantage going in. The GPEN is a 5 day long course followed by a multiple choice exam. Whereas the OSCP can take up to 3 months of practice and ends with a 24 hour, hands on hacking fest. You will learn MUCH more from the OSCP.
Additionally, the OSCP is 1/7th to 1/8th the cost compared to the GPEN. If you are looking to get into professional penetration testing I would recommend the OSCP. I believe the GPEN is meant more for defensive security professionals to get an understanding of attacking, rather than make them pen testers.
What I Wish I Knew Going In
1. Be careful with your usage of Metasploit. It’s a great tool and one that can come in handy on a penetration test, however the exam has specific rules that limit the use of it. As such, it would be best to go through the labs with as little usage of it as possible. There are exceptions however. In some cases you may not be able to find a public exploit for a vulnerability that doesn’t use Metasploit. You have two options at that point, reverse engineer the exploit to create your own OR use Metasploit. I’d tell you to use Metasploit but that’s your call.
2. The public network is for the boring. While I wouldn’t say there is a difference in difficulty, I would argue the true value of the labs comes in when you are pivoting from one network to another. That experience in pivoting is very beneficial and a ton of fun.
3. You NEED to do post-exploitation procedures. Dump passwords, search for hidden files, check the arp cache and the routing table. The OSCP is trying to simulate a live environment and these systems do communicate with one another. You may need to learn something from one box to take down another.
4. The exam guide is found here. Memorize it.
5. When pivoting, use Proxychains. You may tell yourself, “Holy cow, I just found a way into X network! I don’t want to waste time learning how to use Proxychains. I’ll just use the portfwd feature of Meterpreter to go faster”. Trust me, Proxychains requires very little effort to learn and it will be very beneficial.
6. Practice your Buffer Overflows. They are an important part of the course and something that will lead to the OSCE.
7. Do the lab report. Doing so will be excellent practice for the exam report and you can potentially earn 5 points.
8. Create an exam report template ahead of time. After you’ve spent hours working on the exam machines you aren’t going to want to figure out the minute details of report writing. That is why you should create an exam template ahead of time, so you can just drop your screenshots in and describe your results.
What Makes the OSCP So Difficult?
This was the biggest question I had going in. I only recently graduated college, with minimal professional security experience going in, and reading reviews of much more experienced people made me nervous. One person had over twenty years of experience and still failed the exam! If that was the case, how could I ever hope to pass?
If you have the same fears, let me quell them a bit. The OSCP is not that hard. It is specifically an introductory certification.
But why do so many people fail? I have a theory. The key is to note that the OSCP (as much as it tries to be) is not made of REAL systems. It was designed such that a student could go from outside to root in a matter of hours. As a result there are subtle hints and tells that any hand-crafted vulnerable system will have. If you are a professional penetration tester who doesn’t happen to have a ton of experience with CTF’s you would likely fail because you aren’t used to this dynamic.
Ultimately I think this is what trips people up and causes a lot of issues. If you take your time, go through the standard vulnerable tropes, and #TryHarder you’ll ace the exam.
Conclusion
It was a long road and one I thoroughly enjoyed. I’m very proud of my exam results and that I passed on the first attempt. I highly recommend the OSCP to anyone looking to get a technical edge in Information Security.