Intercept Linux CLI Tool Traffic
January 11, 2020
Recently I've been looking into flaws in a handful of Linux CLI tools. Many of these tools interact with APIs on remote systems. Obviously being able to intercept and inspect that traffic is very helpful for security researchers, Pentesters, Red Teamers, bug bounty hunters, or whatever you call yourself.
The following is a simple means of intercepting the traffic of Linux CLI tools with Burp Suite. For reference, all of this testing was performed on an Ubuntu 19.10 VM.
Step 1: Set a Proxy for Our Shell
First things first, we need to set up our proxy. This can be done very easily in many shells such as Bash and Zsh. The following commands will do this:
$ export http_proxy="http://192.168.122.1:8080"
$ export https_proxy="http://192.168.122.1:8080"
Here, 192.168.122.1 on port 8080 is where I have my Burp proxy listening (I use KVM and this is the default subnet VM's spawn on in case you are confused). So far so good. We can actually start intercepting traffic. For example, here I am curling my website.
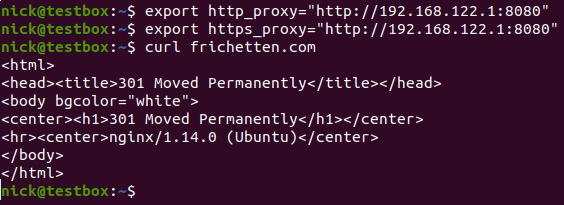
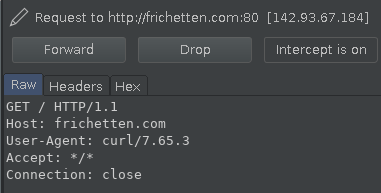
Fantastic, it looks like that gives us a 301 response (redirecting us to the https version of the site), what happens when we follow it?
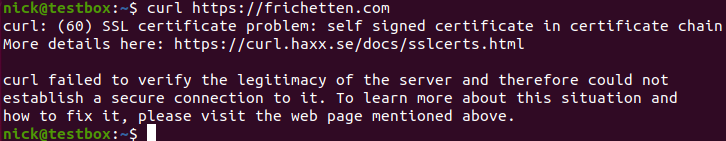
Ah, that's right. Tools should validate the TLS/SSL cert and drop the connection if they aren't correct (if the tool you're looking at doesn’t do this, that's a finding). In this instance, Curl is behaving appropriately and many tools will give you this same response. How do we get around this?
Step 2: Import the Burp Suite Cert in Ubuntu
Many folks who have used Burp Suite to intercept traffic from a browser will be familiar with this problem. The browser sees that the proxy uses PortSwigger's CA and then drops the connection. This is a simple fix with a web browser, but what about with an OS?
On Ubuntu it's actually pretty simple (and presumably simple on other Debian distros like Kali). First we need to download that cert.
$ cd ~/Downloads
$ wget http://192.168.122.1:8080/cert
The file we just downloaded is in the DER format. We need to instead convert it to ".crt" and move it into the "/usr/local/share/ca-certificates" directory as shown below.
$ openssl x509 -in cert -inform DER -out burp_suite.crt
$ sudo mv burp_suite.crt /usr/local/share/ca-certificates
Our final step is to run "update-ca-certificates" which will update our certificates under "/etc/ssl/certs".
$ sudo update-ca-certificatesNext, we can test out our changes by curling an SSL or TLS website.
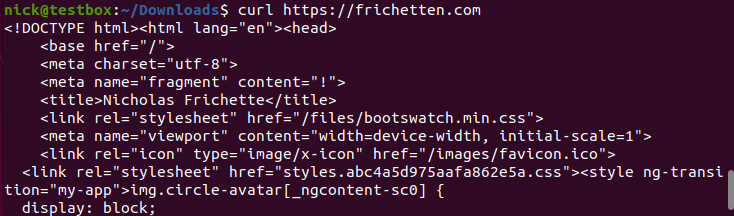
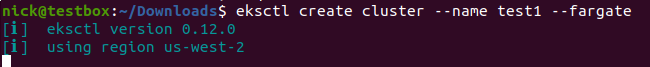
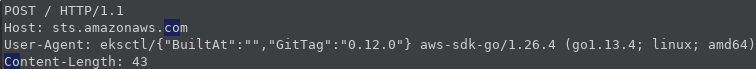
And there you have it. We can now intercept SSL traffic of some Linux CLI tools. For example, eksctl which is a tool to interact with AWS EKS.